Google Advanced Protection
Last week, Google has added a new set of security features in Gmail called “Advanced Protection”, specifically for high-risk users. It was widely covered the media (Wired, The Verge or Reuters) and quickly started a debate about whether Google is the most secure email provider on the planet or if ProtonMail can compete. The main point here to me (and it has been said by many other people everywhere) is whether you trust Google to keep your data or not, depending on your threat model and your opinion about privacy.
But it does not mean we should not understand what Google proposes to do here. This blog post intends to detail these security features and test them.
Google Advanced Protection
Here is what Google includes in the Advanced Protection (according to the Google page and Wired):
- Log in on Desktop only with a 2 factor authentication USB device
- Log in on smartphone only with a 2 factor authentication Bluetooth device
- Blocking non-Google apps from accessing Gmail or Google Drive data
- Google malware scanner will do more in depth analysis and detection
- If you loose access to your account, you will have extra steps to recover access to it
USB Universal 2 Factor Authentication on Desktop#
With Advanced Protection, authentication on your Google account will only be possible with an USB key as second factor (i.e. in addition to your password). These devices have been more and more common for the past years following the development of the Universal 2 Factor Authentication (U2F) standard which allowed different manufacturers to develop such products. This type of second factor is much more secure than text messages (which can be read or stolen either by exploiting issues in the phone network, or by abusing your phone provider) and apps on your phone (which are good but can still be abused by compromising your phone).
You can find the list of 2Fa dongles here, the most common being the Yubikey which costs around 18USD.

U2F USB dongles are now accepted by many platforms (Github, Dropbox, Facebook… you can find the list here). You can use them with Chrome and Opera too. Firefox will support it soon- there is an extension for it but I could not make it work on my laptop.
Bluetooth U2F Dongle#
As USB devices are not an option for smartphones, the solution is to use a Bluetooth U2F dongle. For now, Google proposes to use the Security Key made by Feitian (you can find it on Amazon for ~25USD)

Blocking Non-Google apps#
To me, that’s one of the main benefit of Advanced Protection. Standard Google accounts allows external applications to access Gmail/Google Drive data through the OAuth2 protocol. You see this feature in many websites who use your gmail account for authentication, but it can also be used to request full access to your emails and data. This feature became largely known in May when a large phishing campaign used this trick to propagate to victim’s contacts, but we knew since April that this feature had been used in APT28 phishing campaigns.

Example of an OAuth app requesting full access to emails (Source: TrendMicro)
Google also allows you to define application passwords, which are passwords you can use for specific applications to access your emails without second factor (commonly used for Thunderbird/Outlook).
The drawback of this protection is that many third party apps will be blocked. According to Google, it is only possible to access Gmail through your browser (no Outlook or Thunderbird), and Apple apps on iOS (Mail, Contact and Calendar) won’t work. You will have to use Google apps.
Google Malware Scanner#
This feature is not clear to me. Google mentions where they use this (in May they published about how they now use machine learning for malware detection in GSuite for instance), but not really on how they implement it.
According to Wired, this feature would delay email reception by more than 60 seconds. My guess is that either they use dynamic analysis on attached files for malware detection, or they request the content of links included in emails to check for malicious pages (which seems more likely as this feature was added in GSuite recently).
Extra Steps for Account Recovery#
The implementation of this feature is not clear either. Google explains that “Advanced Protection adds extra steps to verify your identity. If you ever lose access to your account and both of your Security Keys, these added verification requirements will take a few days to restore access to your account”. For now, Google uses different methods to confirms that you are the owner of an account (any 2FA you could have, recovery address and also the creation date of the account or a secret question). It is unclear to me what changes in this process (and Google likely won’t communicate about it).
Step by Step Guide
So let’s do this. First go on the Advanced Protection page : https://landing.google.com/advancedprotection/

Google asks confirmation that you own both U2F devices, or proposes to buy this one and this one. I only have USB devices for know but it should be enough for tests.

Then it requires you to install 2 security keys :

As I don’t have a bluetooth dongle yet, I am adding two test YubiKeys

Last confirmation:

Success!

Tests
Let’s first test the delays due to the malware scan:
- For text only emails, I have not seen any delay at all
- For links, I have not experienced any delay (but it may be because they were already known by Google)
- For an attached file (I tried with a doc), it was delayed around 2 minutes
Next let’s test access to Gmail and Gdrive, I have used the OAuth playground to try OAuth2 access :
- I was able to access calendar and contact information
- both Gmail and Gdrive were indeed blocked :
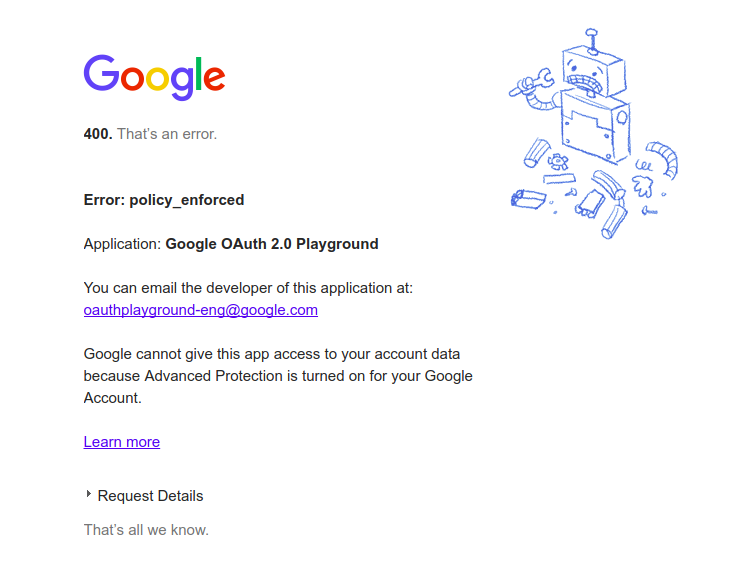
Finally, I tested Application Passwords. Application passwords are just not available anymore in the interface.
I tried to recover the account by giving the creation date and an unrelated email but I got this question :
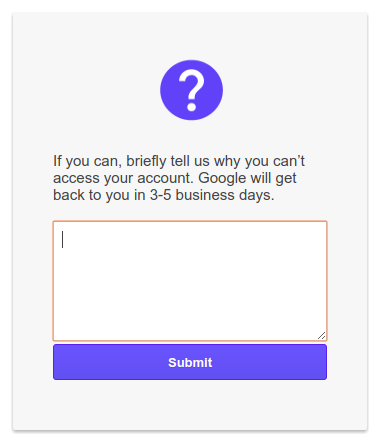
It does not seem to be different to me from a standard account, but Google may have different processes for the manual background checks, hard to know.
Conclusion
Besides the recurrent is-Google-in-your-threat-model question, I find these features interesting as it clearly increases the security of your account (especially for app specific access which is more and more used in phishing attacks). But as John-Scott Railton has rightly argued, security features are not efficient if they are intended for high-risk users only and disabled by default. Some people will indeed be ready to take time and accept usability tradeoffs to increase their security level, but it is likely that a majority of high-risk users won’t take such steps for thousands of different and legitimate reasons (from a lack of time, to a real need to use some softwares). Or even more likely: they don’t consider themselves as high-risk users (many activists are not aware of these risks).
Google should invest time and effort into bringing these improvements for common users, and in some cases it could be done pretty easily. Let’s take OAuth2 authentication for instance: I think 99% of users don’t use OAuth for anything other than authentication. It would make sense to have access to sensitive data (emails, drive and calendar) blocked by default in Gmail with an easy way to unlock it. Suddenly 99% of users become protected against OAuth phishing versus years of trainings to explain what is OAuth and how it can be abused (which is what we are doing right now).
Thanks to Starcat for their help :). You can contact me on Twitter if you have any comment or feedback on this article.