Targeted Attacks Against Civil Society : What is New in 2019?
TL;DR#
New trends in targeted attacks against civil society in 2019 :
- More attacks against smartphones, some attacks are using 0-days and we don’t know how to be effectively protected against them, but many attacks are using exploits against fixed bugs in Android
- Phishing attacks bypassing 2 Factor Authentication solutions other than hardware keys are common now. We have to consider that most attacks will support that in the future, and move to hardware tokens for 2FA
- OAuth attacks are still there and will likely be there for some time. As they bypass many protections against phishing, people need to be aware of them and check their OAuth access regularly.
Targeted Attacks Against Civil Society : What is New in 2019?#
10 years ago, the GhostNet report published by the Citizen Lab made quite a buzz; it described an important coordinated effort of compromising computers over the world, from the embassy of India in the US to PetroVietnam. It was one of the first times that an attack campaign of that scale was revealed, but what made it especially important is that this campaign was discovered when researchers identified attacks against the Tibetan community in exile, and more specifically against the Office of the Dalai Lama.
We have now a way better understanding of these attacks against civil society, with multiple examples in different regions and using different techniques, mostly thanks to the work of few research labs and non profit organisations like the Citizen Lab, Amnesty International or the EFF, but also from the security industry, often covering attacks targeting the industry at the same time (you can find a list of these reports currated by Claudio Guarnieri here).
The digital landscape has changed quite a bit in the last ten years. There are now more groups supporting civil society and Human Rights Defenders at the intersection of technology and security, with security trainings, collaborative maintenance of civil society websites, events to talk about technology and human rights. Yet, there is still a gap between security researchers precisely following the moving landscape of targeted attacks and people supporting civil society with trainings and technical support. I hope that this blog post can help bridge this gap by summarizing important changes in targeted attacks over the past year.
More Attacks Against Mobile Phones#
This year, we have seen confirmation that there are increasingly more attacks targeting smartphones today than there used to be, mostly in connection with three important events :
- In August 2019, Google Project Zero published an article describing the utilization of iPhone 0-days in watering hole attacks on compromised Uyghur-related websites. It is the first time we have seen 0-days used in watering hole attacks, which forces us to reconsider our view of 0-days used only in very targeted attacks. It appears that the same attack framework was used against Tibetan groups at the same time using only old days exploits.
- In October 2019, Amnesty International published a report describing attacks against Moroccan Human Right Defenders using text messages containing NSO-related links that would use 0-days to exploit the browser on click as it was seen before, but also by injecting malicious code into the mobile phone traffic. This network injection allows to do a no-click exploitation of the smartphone.
- We have more examples of 0-days attacks done by NSO groups, showing that some of these attacks are exploiting chat applications such as WhatsApp or iMessage, but also exploits in Linux kernel to exploit Android phones. The WhatsApp bug exploited in May 2019 by NSO Group prompted a strong reaction by WhatsApp: first suing NSO Group for this attack, and also informing all the people targeted, which led to discover attacks against activists in India, Ghana and Rwanda (among the more than 100 human rights defenders and journalists).
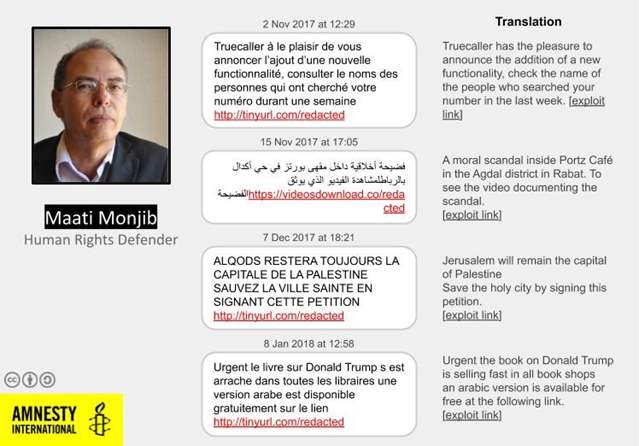
Example of attacks against Maati Monjib, a Moroccan Human Right Defender (Source: Amnesty)
Mobile phone 0-days are there and we have no good ways to be protected against them#
There are 0-days attacks against smartphone using one click (a message with a link that the target need to click on) or 0-click (no action needed from the targets) attacks available to dedicated groups with sufficient funds. There is no easy way to be protected against them. We either have to limit the attack surface available for these tools (for instance, by disabling iMessage on iPhone if you do not need it, or by using fewer chat applications), or assume that some devices are compromised if these types of attacks are in our threat model.
This topic is definitely an important one that we have to work on collectively, but we should not forget that most attacks today do not need to use 0-day to be successful, and keep in mind that attacks using known vulnerabilities are far more common against civil society.
In most cases, 0-days won’t be needed to compromise a smartphone#
All the discussion about 0-day should not make us forget that most attacks are technically really simple. And they work. This is also true for attacks against smartphones. For anyone buying a random android phone today, the chances are high that the phone is not freshly updated and may not have updates available (this depends on the country of purchase, and the price range of the phone, which creates an important inequality on smartphone security).
Attackers understand this, Tibetan groups were targeted this year by an attack framework that was only relying on fixed old-day vulnerabilities, one for iOS and 8 for Android. In most cases, the attackers only had to get the exploit code from the Chrome bug tracker and adapt it to be able to exploit it in the wild.
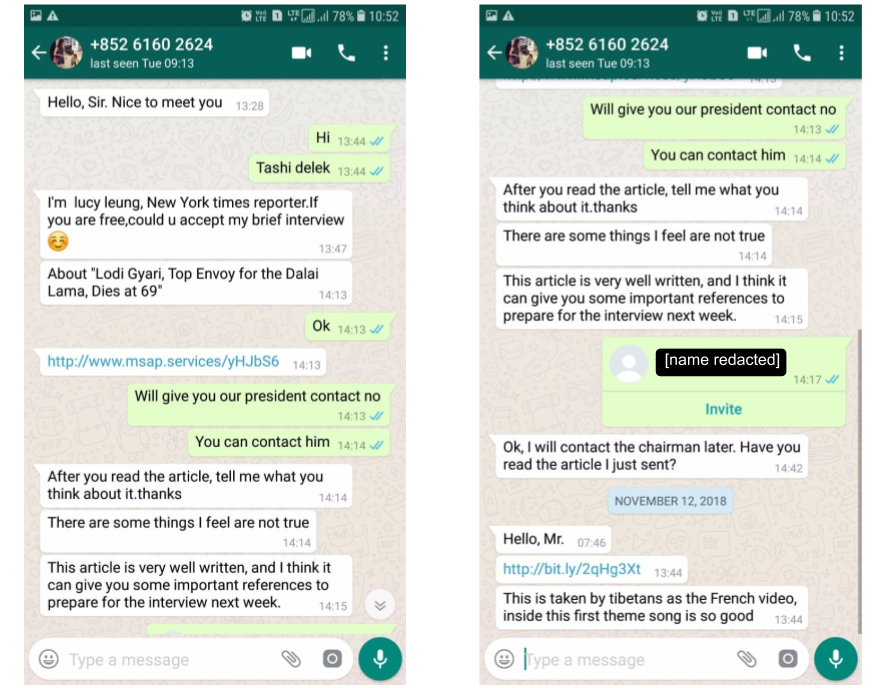
Example of attack against Tibetan human right organization (Source: Citizen Lab)
What can we do ?#
There are a few things we can do against this threat :
- Secure our smartphones as much as possible : ensure that system and critical apps (such as browsers and chat applications are updated, and reduce the attack surface as much as possible (by disabling iMessage, limiting the number of chat applications, avoiding using SIM if possible and using a VPN on insecure networks)
- Consider that smartphones can be compromised : in cases where there are suspicions that 0-day could be used, considering that smartphones can be compromised and take it into account in the threat model can allow to limit the impact of the attack
- Connect people at risk of being targeted by these attacks with research groups like Citizen Lab or Amnesty Technology : there are few people in the world targeted by these attacks and few people who know enough to be able to analyse them and find solutions, we have to make sure these people work together (ping me if you don’t know who to contact)
References :
- Sept 2019 : Missing Link - Tibetan Groups Targeted with 1-Click Mobile Exploits by the Citizen Lab
- Oct 2019 : Morocco: Human Rights Defenders Targeted with NSO Group’s Spyware by Amnesty International
Phishing Kits supporting 2FA Bypass are Common#
For many years, one of the main solution against phishing has been to recommend the use of 2 Factor Authentication. 2 Factor Authentication (2FA) is using secondary means of authentication in addition to the password. There are three common ways to do 2FA (ranking from the least secure to the most secure) :
- Temporary code sent by text message (SMS have a lot of security issues)
- Temporary code given by an app on a smartphone (such as FreeOTP)
- Hardware token like Yubikeys
In 2019, we received confirmation that attackers are now commonly using phishing kits that are bypassing all forms of 2FA except hardware keys :
- In December 2018, Amnesty International described an attack campaign in Middle-East supporting 2FA bypass
- There are now also several open-source phishing kits supporting bypassing some forms of 2FA available online such as Modlishka or ReelPhishing; they were extensively covered by technical press in January 2019
All of these phishing kits are bypassing all forms of second factor authentication except hardware keys. Hardware keys are more robust and not vulnerable to these attacks; the key provides the temporary code to the domain through the browser but only after confirming that the current domain matches the previously registered domain. Therefore, classic techniques, like using a domain similar to a real one (gooogle.com instead of google.com, for example) are completely ineffective with it.

We have to expect that all phishing kits will support bypassing most forms of 2FA in the future, and promote and provide hardware security keys to human rights defenders.
References :
- Dec 2018 : When Best Practice Isn’t Good Enough: Large Campaigns of Phishing Attacks in Middle East and North Africa Target Privacy-Conscious Users by Amnesty International
- Open-source phishing kits supporting 2FA bypass : Modlishka, ReelPhishing
OAuth Attacks are Still There#
Open Authentication (OAuth) is a protocol designed for access delegation and has become a popular way for major platforms (Facebook, Google, Twitter, etc.) to permit sharing of account information with third party applications. For some years now it has also been used in phishing campaigns against civil society: first by groups with a high technical level such as APT28, then by groups with significant lower technical skills.
OAuth phishing is a rather basic technique but it is very effective for one reason : it defeats most recommendations given to users against phishing websites. Most trainings advise to check the domain name or the content of the page, but with OAuth phishing an actual Google page is shown to the user to request access to their account. If the user has never heard about OAuth, it is quite easy to misunderstand what is happening and fall into it. Two Factor Authentication does not help with OAuth phishing either as the user should be legitimately logged with their Google account.
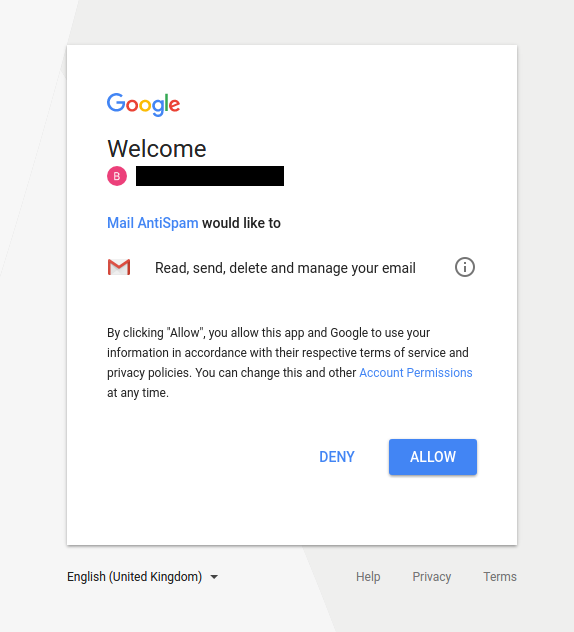
Example of OAuth phishing attacks targeting Tibetan activists in 2018 (Source: Citizen Lab)
When these attacks appeared, Google (in likely addition to other major platforms) started to take measures to make these attacks more difficult, by adding a verification process to OAuth applications requesting sensitive scopes, and initiating some threat investigatons to block malicious applications. Google has also added an Advanced Protection feature that disables OAuth access to email and documents.
For quite some time, I thought we would see a drop of OAuth phishing in 2019. It turns out I was wrong. Many examples of OAuth phishing this year shows that Oauth phishing is still regularly used against civil society and that, more importantly, these attackers are using new tricks to bypass Google protections. An Amnesty International report from Summer 2019 describes OAuth phishing attacks requesting targets to give access to a legitimate third party application, and used social engineering to try to convince them to share the access key with the attacker. While the technique may not be especially effective, it is clever and shows that attackers are still exploring new ways to abuse OAuth access.
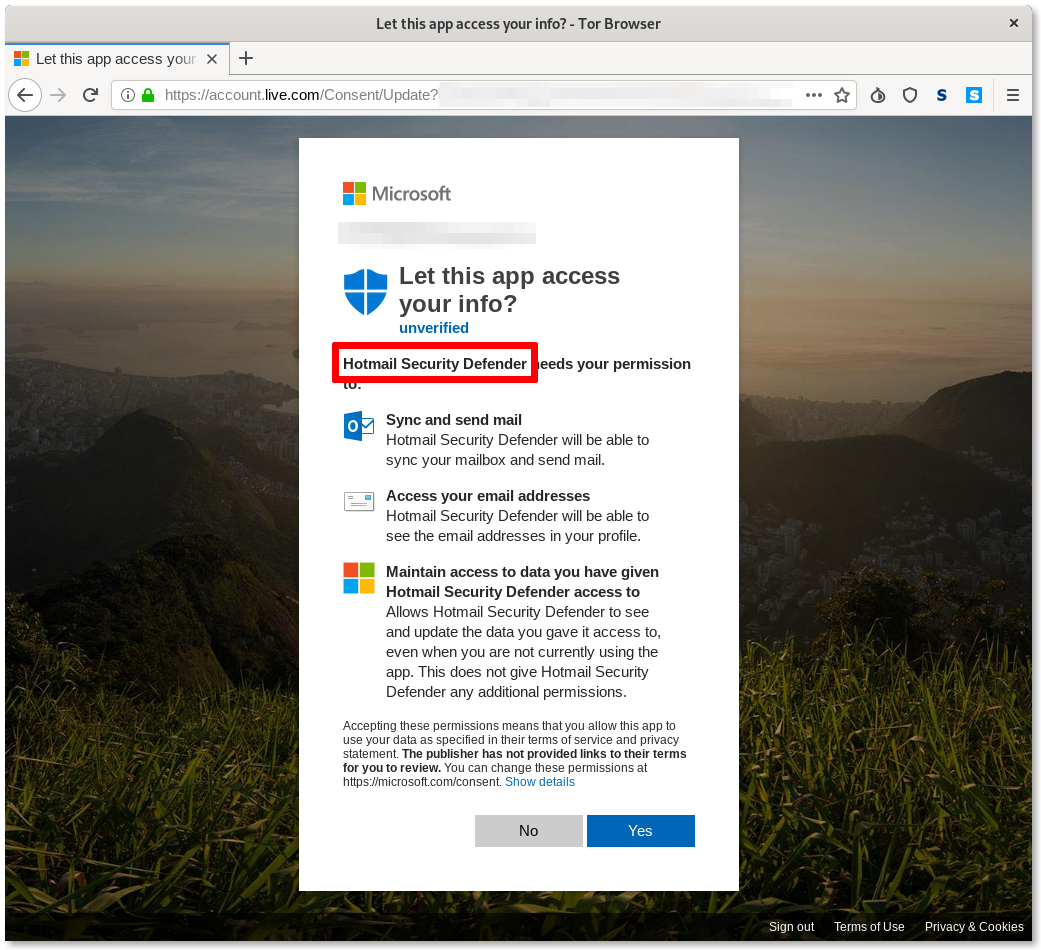
Example of Outlook OAuth phishing attack targeting MENA journalists in 2019 (Source: Amnesty)
So OAuth phishing is still here and it will likely be for some time. There are a few things we can do against these attacks :
- Add OAuth phishing examples to security trainings
- Regularly check third party OAuth access (here for Google)
- Google Advanced Protection can be a good solution but can be tricky to set-up
References :
- Jan 2018 : Spying on a Budget - Inside a Phishing Operation with Targets in the Tibetan Community by the Citizen Lab
- Aug 2019 : Evolving Phishing Attacks Targeting Journalists and Human Rights Defenders from the Middle-East and North Africa by Amnesty International
Conclusion#
2019 is almost over, and it has been an interesting and challenging year. I hope this blog post helped you better understand the threats that Human Rights Defenders face today. If you have any questions or comments, or if you think you are being targeted by a possible government-sponsored attack as an activist, feel free to send me an email (tek AT randhome.io).