How to Check if an Android Phone has a Stalkerware Installed?
Stalkerwares are malware used in abusive relationships to spy on someone’s partner. I have talked quite a bit about it already, see my previous blog posts for more background information on stalkerware.
There are different ways to check if a stalkerware is installed on a phone. At Echap, we have written a guide to check for configuration settings on an Android phone (in French). We think it is the easiest way for non-tech people and quite reliable. The Clinic to End Tech Abuse has developed a tool called ISDi to look for stalkerware based on package names on Android and iOS. More recently, Felix Aimé has released a tool called TinyCheck to analyze network traffic from a smartphone, which can be used to identify stalkerware traffic.
In this blog post, I suggest another methodology to detect stalkerware applications on Android phones, based on indicators for stalkerware I have been aggregating. It is intended for a technical audience, mostly tech people who support organizations working with survivors, as it requires some technical knowledge to use the different command-line tools. (I have tested these tools only on Linux, it should work on Mac OS, but no guarantee).
Note: as I have written before, I think we should make sure we are considering all technology-related threats in intimate partner abuses, and not only stalkerware. Both because it does not make sense to draw an arbitrary line on stalkerware as the important issue and because the research done by the CETA seems to show that in many cases survivors think they have a stalkerware installed while the issue is another form of digital surveillance.
Methodology#
Here is the methodology I suggest:
- Enabling USB debugging on the Android device
- Extracting APKs from the phone using snoopdroid
- Checking APKs based on public stalkerware indicators
- Digging more into APKs using sdanalyzer
Enabling USB debugging#
You first need to enable USB Debugging on the phone. To do so, you can follow the official Android documentation, here is the interesting part of it:
On Android 4.1 and lower, the Developer options screen is available by default. On Android 4.2 and higher, you must enable this screen. To enable developer options, tap the Build Number option 7 times. You can find this option in one of the following locations, depending on your Android version:
- Android 9 (API level 28) and higher: Settings > About Phone > Software information > Build Number
- Android 8.0.0 (API level 26) and Android 8.1.0 (API level 26): Settings > System > About Phone > Build Number
- Android 7.1 (API level 25) and lower: Settings > About Phone > Build Number
At the top of the Developer options screen, you can toggle the options on and off (figure 1). You probably want to keep this on. When off, most options are disabled except those that don’t require communication between the device and your development computer.
Before you can use the debugger and other tools, you need to enable USB debugging, which allows Android Studio and other SDK tools to recognize your device when connected via USB. To enable USB debugging, toggle the USB debugging option in the Developer Options menu. You can find this option in one of the following locations, depending on your Android version:
- Android 9 (API level 28) and higher: Settings > System > Advanced > Developer Options > USB debugging
- Android 8.0.0 (API level 26) and Android 8.1.0 (API level 26): Settings > System > Developer Options > USB debugging
- Android 7.1 (API level 25) and lower: Settings > Developer Options > USB debugging
Once it is done, connect the Android phone to your computer with an USB cable. Make sure that adb is installed and check that device is available with the command adb devices :
> adb devices
List of devices attached
RF2F722NU0C device
You can test that the access to the device works using the command adb shell. Once you have confirmed that the adb connection is working, kill the adb server with adb kill-server.
Extracting APKs using Snoopdroid#
Follow the instructions to install snoopdroid.
Then launch the extraction:
$ snoopdroid --storage apks
_ _ _
| | (_) | |
___ _ __ ___ ___ _ __ __| |_ __ ___ _ __| |
/ __| '_ \ / _ \ / _ \| '_ \ / _` | '__/ _ \| |/ _` |
\__ \ | | | (_) | (_) | |_) | (_| | | | (_) | | (_| |
|___/_| |_|\___/ \___/| .__/ \__,_|_| \___/|_|\__,_|
| |
|_| v2.3
*** Retrieving package names ...
*** There are 285 packages installed on the device. I selected 208 for inspection.
*** Starting acquisition at folder apks/2021-01-12T210901
*** Downloading packages from device. This might take some time ...
[1/208] Package: com.samsung.android.provider.filterprovider
Downloading /system/app/FilterProvider/FilterProvider.apk ...
100%|██████████████████████████████████████████████████████| 381k/381k [00:00<00:00, 2.91MB/s]
[2/208] Package: com.sec.android.app.DataCreate
Downloading /system/app/AutomationTest_FB/AutomationTest_FB.apk ...
100%|██████████████████████████████████████████████████████| 348k/348k [00:00<00:00, 3.16MB/s]
[3/208] Package: com.sec.android.widgetapp.samsungapps
Downloading /system/priv-app/GalaxyAppsWidget_Phone_Dream/GalaxyAppsWidget_Phone_Dream.apk ...
100%|██████████████████████████████████████████████████████| 797k/797k [00:00<00:00, 3.48MB/s]
[...]
This process will extract all the APKs installed on the phone in a folder, it should take a little while.
Checking the APKs#
I maintain a list of indicators for stalkerware that include package ids, certificates, hashes, network domains, and IPs, and since recently yara rules. I have developed a python script that checks an APK or a folder of APKs based on the associated indicators.
First, download the repository, either through git (git clone https://github.com/Te-k/stalkerware-indicators.git) or by downloading the ZIP archive. Then you need to install the required libraries with pip install -r requirements.txt. And finally, launch the script on the folder containing the apks:
$ python check_apk.py apks/2021-01-12T210901/apks/
Loaded 76 app ids, 55 certificates, 221 network indicators and 1881 hashes
com.sec.android.mimage.photoretouching.apk : OK
com.samsung.android.net.wifi.wifiguider.apk : OK
com.sec.android.CarrierCodeChanger.apk : OK
com.samsung.android.themestore.apk : OK
com.samsung.android.themecenter.apk : OK
com.sec.android.easyMover.Agent.apk : OK
com.google.android.gms.policy_sidecar_aps.apk : OK
com.samsung.safetyinformation.apk : OK
com.samsung.android.setting.multisound.apk : OK
com.sec.usbsettings.apk : OK
com.android.dreams.phototable.apk : OK
[...]
com.google.android.apps.tachyon_split_config.en.apk : OK
com.android.traceur.apk : OK
1 suspicious applications identified:
- com.android.core.mngp_base.apk : Known stalkerware package id: Snoopza
Here one stalkerware was identified from the Snoopza family.
Analyzing Further APKs with SDAnalyzer#
This first check is only as good as the indicators are, and there are definitely stalkerware products out there not listed yet in the indicator list. So it is worth analyzing manually the APKs to see if we find anything suspicious. I have developed a tool called SDAnalyzer specifically for that purpose. It extracts most useful information from all the APKs and gives you a nice interface to analyze them.
You install sdanalyzer easily with pip install sdanalyzer.
Then you need to import the APKs into a device. First, create a device with SDanalyzer:
$ sdanalyzer phones --create "Germain's Phone"
1 Germain's Phone None
Then import all the APKs in the folder in the device with the corresponding id (1 here above):
$ sdanalyzer import --phone 1 .
Importing ./com.sec.android.mimage.photoretouching.apk
APK ./com.sec.android.mimage.photoretouching.apk added to the phone
Importing ./com.samsung.android.net.wifi.wifiguider.apk
APK ./com.samsung.android.net.wifi.wifiguider.apk added to the phone
Importing ./com.sec.android.CarrierCodeChanger.apk
APK ./com.sec.android.CarrierCodeChanger.apk added to the phone
Importing ./com.samsung.android.themestore.apk
APK ./com.samsung.android.themestore.apk added to the phone
Importing ./com.samsung.android.themecenter.apk
APK ./com.samsung.android.themecenter.apk added to the phone
Importing ./com.sec.android.easyMover.Agent.apk
APK ./com.sec.android.easyMover.Agent.apk added to the phone
Importing ./com.google.android.gms.policy_sidecar_aps.apk
It looks like that no app name is set for the main activity!
APK ./com.google.android.gms.policy_sidecar_aps.apk added to the phone
[...]
The import will take 5 to 10 minutes depending on the number of APKs. You have to wait until the end of the import before doing the analysis (due to the impossibility to do concurrent access to the SQLite database).
Then you can launch the web interface with sdanalyzer serve. It will open the interface directly in your browser:
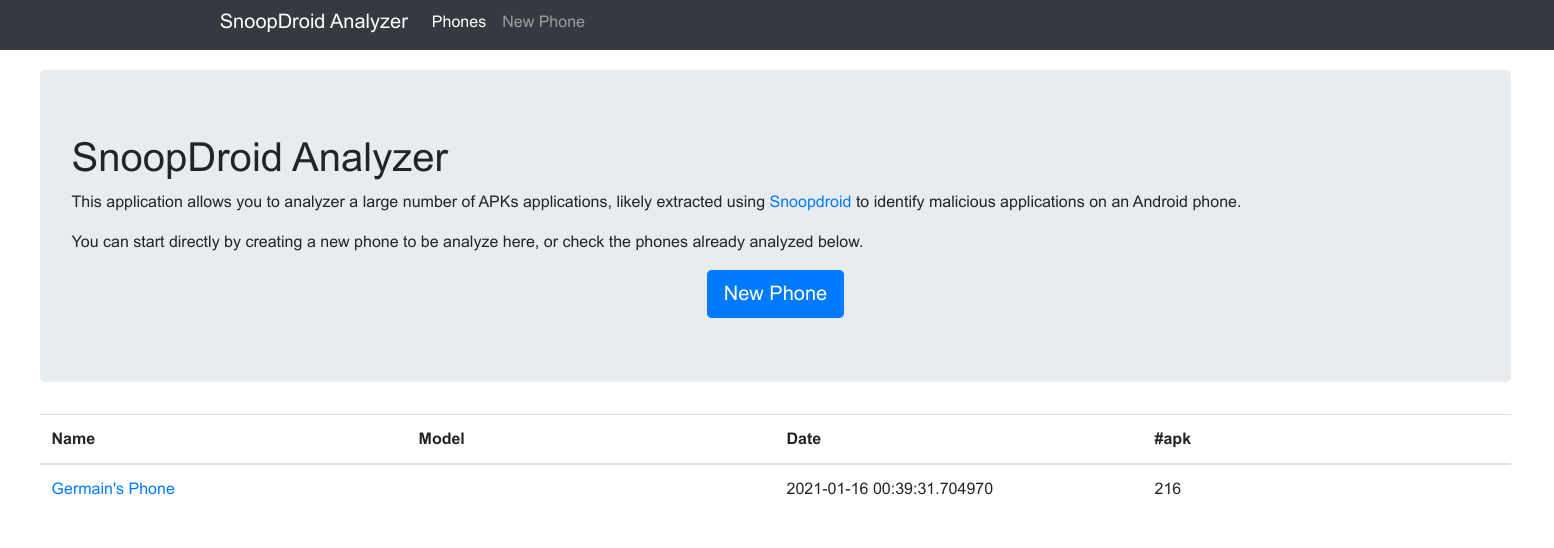
Select the phone you just created to see the list of APKs:
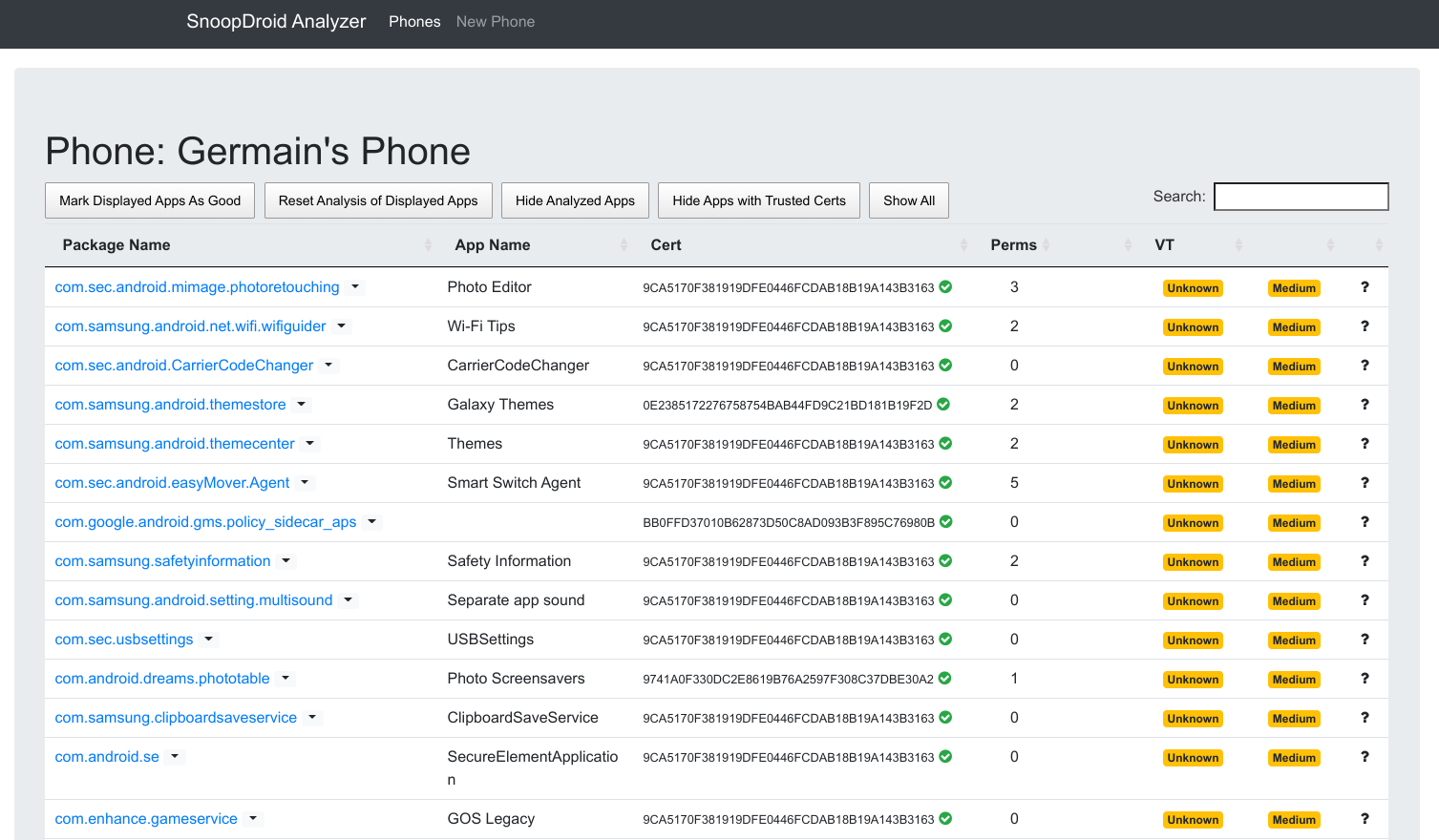
In this table you see several useful information:
- The package id
- The App Name
- The Certificate, including a green tick if I consider this certificate trusted
- The number of sensitive permissions the app is requiring (malicious apps like stalkerware always require a lot of permissions)
- A marker (called frosting) if the app was downloaded from the Google Play Store
- The result of the Virus Total analysis (currently not working due to a bug in Virus Total platform)
- A threat level evaluated based on all the information (take it just as a hint and not as something very reliable)
You can click on any application, and have a more detailed view of it:
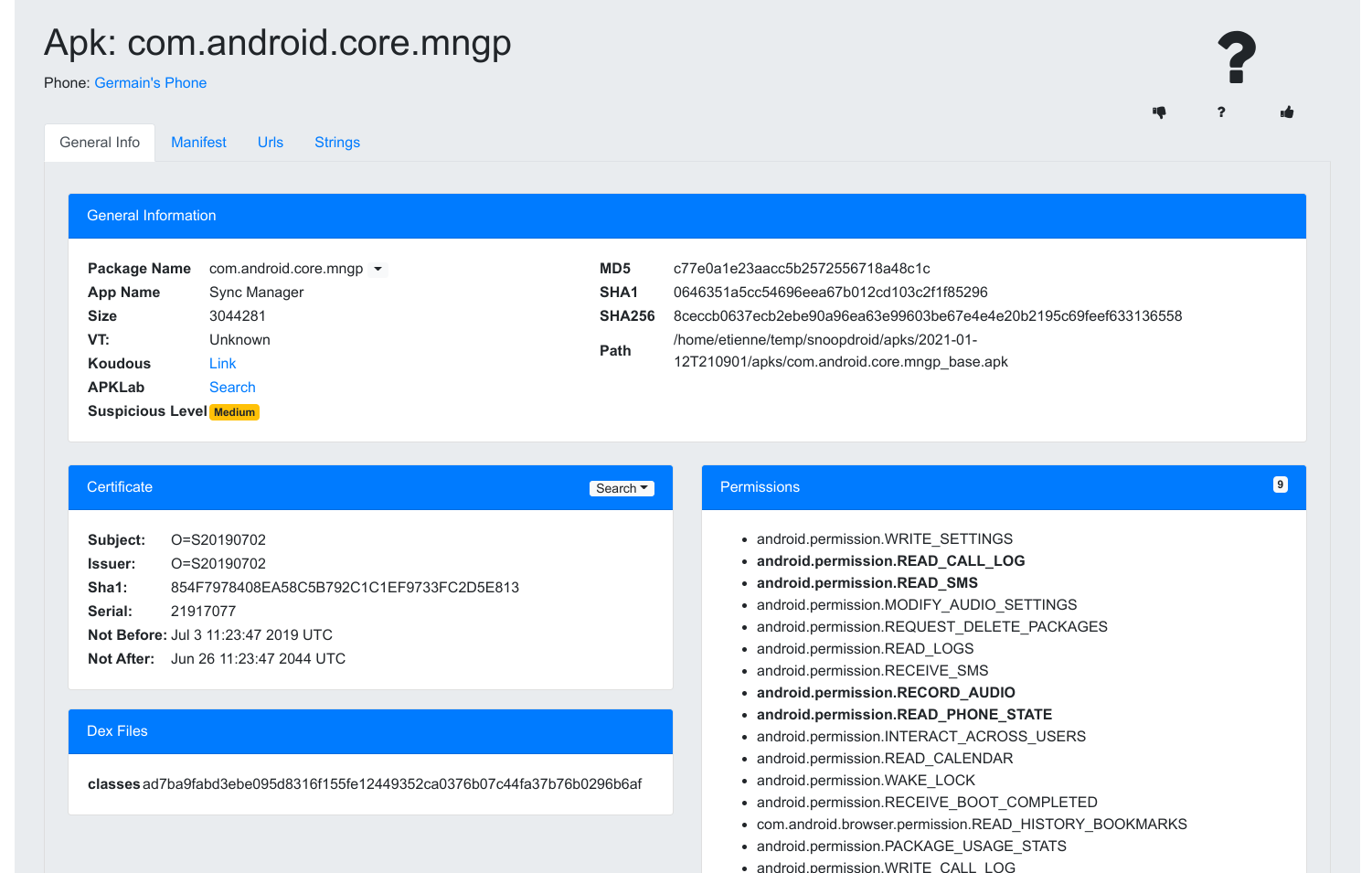
On that page, you have different information and links:
- Information on the package
- Links to check for the app in VirusTotal, Koodous and APKLab
- The certificate that signed the app
- The full list of permissions required (with the sensitive one in bold)
- The full manifest
- A list of urls extracted from the DEX files
- A list of strings extracted from the DEX files
It can be a lot of information at first and very time-consuming to process everything. Here are some hints of what you should look in priority:
- Check the VirusTotal result (when it will be fixed by VT). Any app with more than 5 detections is clearly suspicious. Between 1 and 5, it can be a false positive, you should check the app in detail. If it is unknown, it is unusual (but happens for some system packages), you should check the app in detail
- You can safely discard the apps marked as having a legitimate certificate (check before the VT results of those just in case).
- Check the number of permissions, stalkerware apps usually require more than 15, including most of the sensitive one (SMS, calls, etc.).
- Most stalkerware apps are installed outside of the market, so there should not be frosting (but as it can be added manually without changing the signature, it is not fully reliable).
When you have looked at an application, you can mark it as suspicious or legitimate in the web interface and hide the apps already checked in the main list, so that you can only see what is still to be analyzed. If you have doubts about an application, it can be useful to search for other applications signed with the same certificate on VT, Koodous, or APKLab and see if they look legitimate or suspicious.
This process more time-consuming and less reliable than using indicators. Take some time to understand what every field means, the first phone will be a bit hard with so much data, but you will soon get used to the process and able to identify suspicious apps quickly.
Once you have finished the analysis, you can delete the data extracted with sdanalyzer flush.
That’s all, Folks!
I have used that methodology several times to search for malware and it is quite reliable and quick after some practice. The challenge here is to build a solid stalkerware database, to avoid spending too much time in SDAnalyzer, so feel free to contribute to the stalkerware indicators.
If you have any comments, feedback, or thoughts on this process, or if you are working with organizations supporting victims of domestic violence, feel free to get in touch by email or by Twitter DM.
This blog post was mostly written while listening to KOKOROKO